What is AES-256
AES-256 is the first and only publicly accessible standard which was approved by NSA (US National Security Agency) to protect top secret information. 256 refers to the number of transformation rounds (14) which convert the input (origin) into the output (ciphertext). AES is a symmetric key algorithm, which means that same key is used to encrypt and de-crypt the data.
How AES-256 implemented in Ubuntu
AES-256 is implemented via LUKS (Linux Unified Key Setup) based on cryptsetup and dm-crypt. With LUKS both partitions and boot loader are encrypted. The latter means that you will be prompted to enter your passphrase at boot to decrypt and load OS. Other supported by LUKS encryption modes are CBC, ESSIV, SHA-256.
Setup
Ubuntu 20.04 setup starts with default things like language select, updates and network setup. We will not be focusing much on this, because it’s pretty straightforward. You can check these steps on the Pictures 1 and 2 below.
Ubuntu ISOs can be found on the official website: https://ubuntu.com/download
We do not need network very much for this setup, so I skip it.
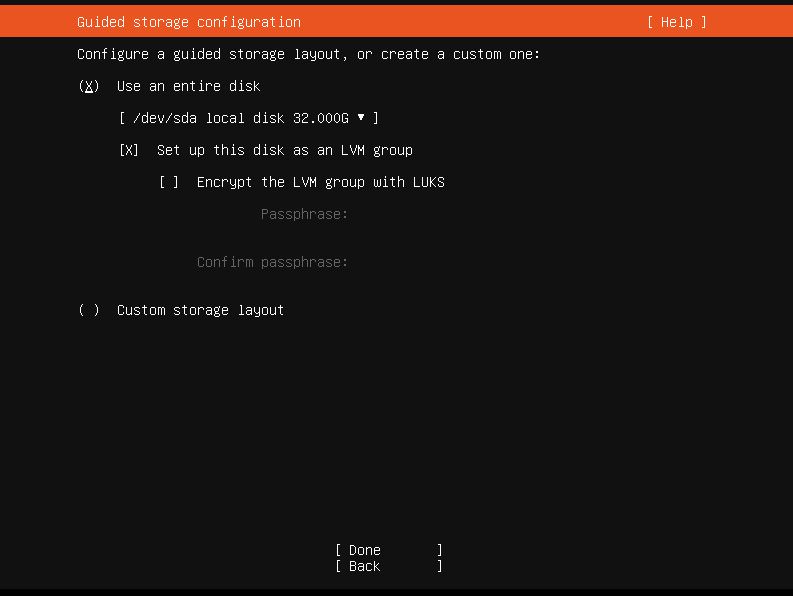
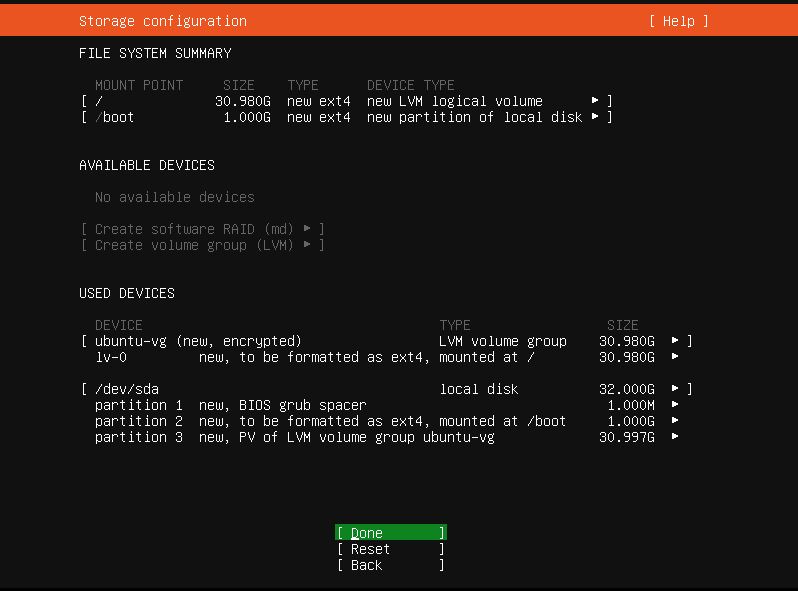
Once you are on the storage configuration (pic. 3) page, you will need to select “Encrypt the LVM group with LUKS” and create your passphrase. Important, make sure that this passphrase has very strong difficulty because it’s used to decrypt the partition.
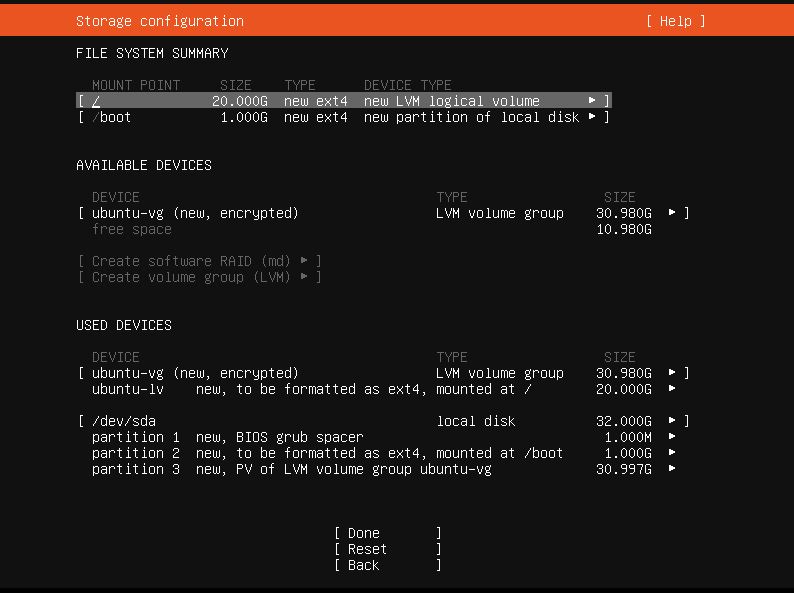
Next you will be directed to the partitioning page. Default partitions look like on pic. 4. If check, you will see that there is a default LVM mounted which is not encrypted (ubuntu-lv). We need to unmount and delete it.
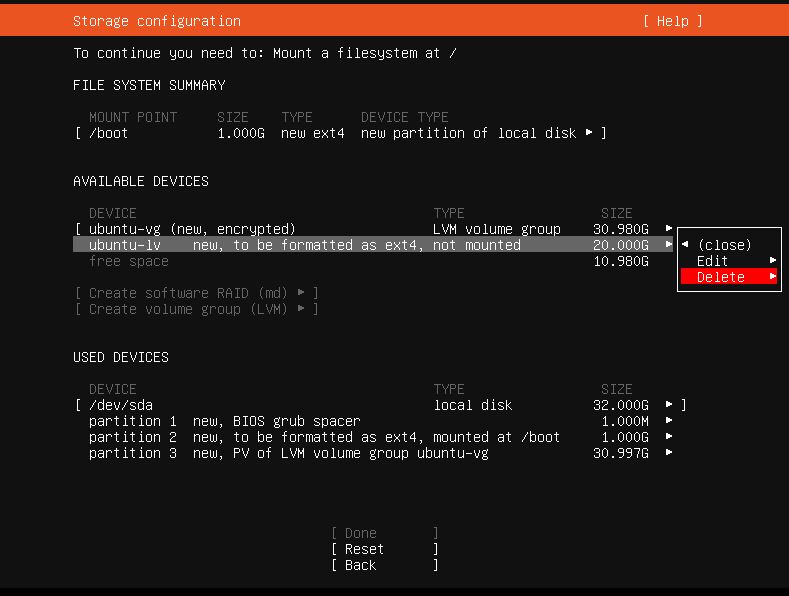
After we have deleted the ubuntu-lv, like it’s shown on pic. 5, we are ready to create new encrypted Logical Volume (pic. 6 and 7).
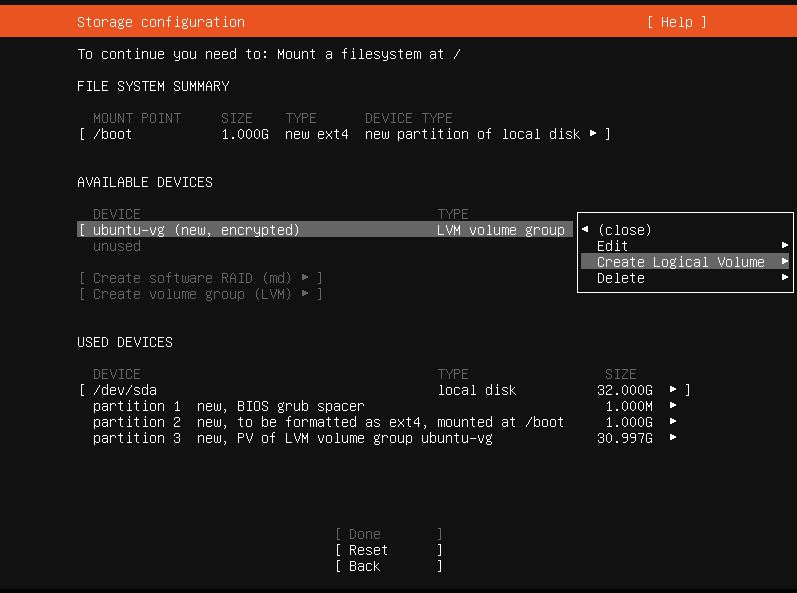
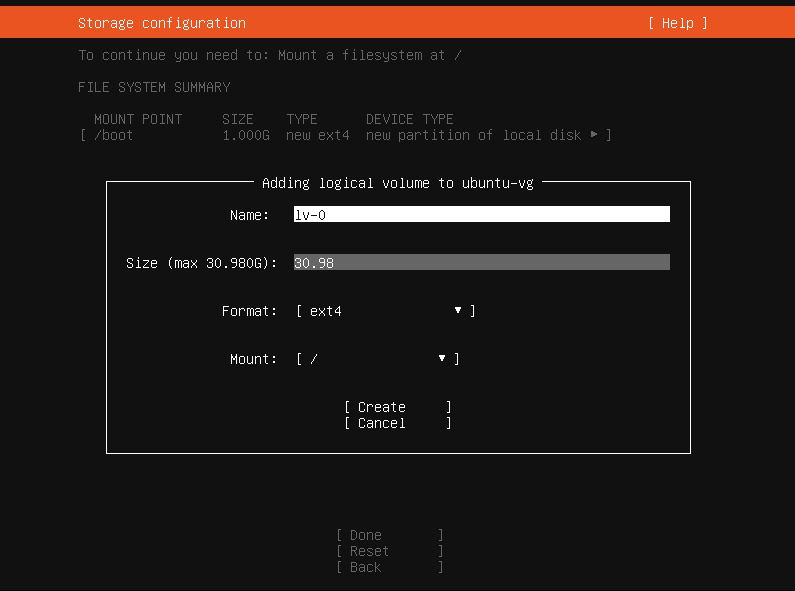
Enter full Size of the partition and press Create.
After all, your partitions should look like that (pic. 8).
After you finish partitioning, you will be asked to name your server and create username and password. These are regular login details and not for decrypting your disk.
Done.
Done.
Reboot Now
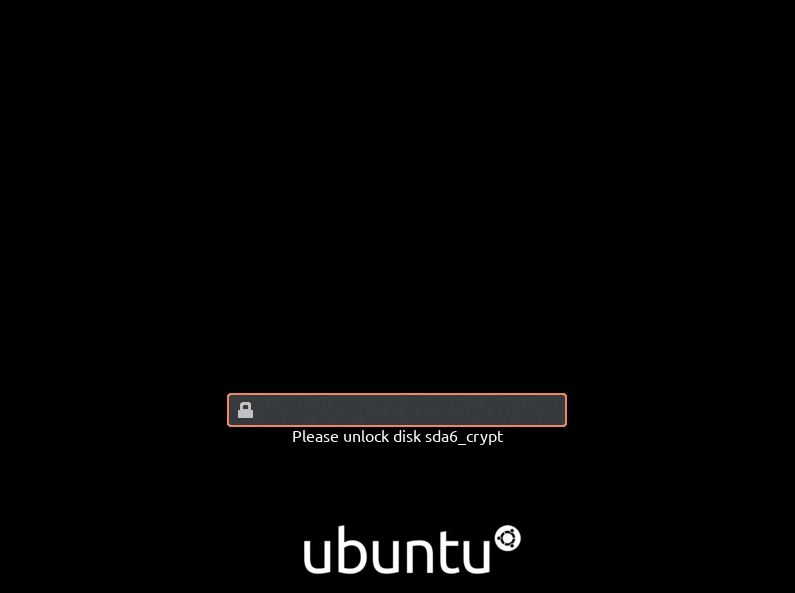
At boot you will be prompted for passphrase to decrypt your disk. Important, forgetting the password means all your data is lost.
If you do not want to deep dive into encryption technologies yourself, we at yohost.org can offer ready-to-go encrypted remote desktops. Different operating systems are available, including Windows.