PGP stands for Pretty Good Privacy – encryption software which uses a combination of hashing, symmetric-key and public-key cryptography for secure data communication. The first version of PGP was created in 1991 by Phil Zimmermann. Read more about PGP in Wikipedia.
How it works in simple words
PGP works by creating a key pair – public and private. Public key is shared among the senders and used to encrypt messages/files. Private key is used to decrypt emails and files encrypted with the public key. For example, Mike wants to receive an encrypted email from Joe. For this, Mike creates a key pair and shares his public key with Joe. Then Joe creates a message, encrypt it with Mike’s public key and sends it. Mike receives an encrypted message and decrypts it with his private key.
How encrypted email looks like?
On the Picture 1 below you can see how encrypted email sent to Gmail looks like. This email consist of two parts – one part is not encrypted and another part is encrypted. One cannot know the content of encrypted part without private key of the intended recipient.
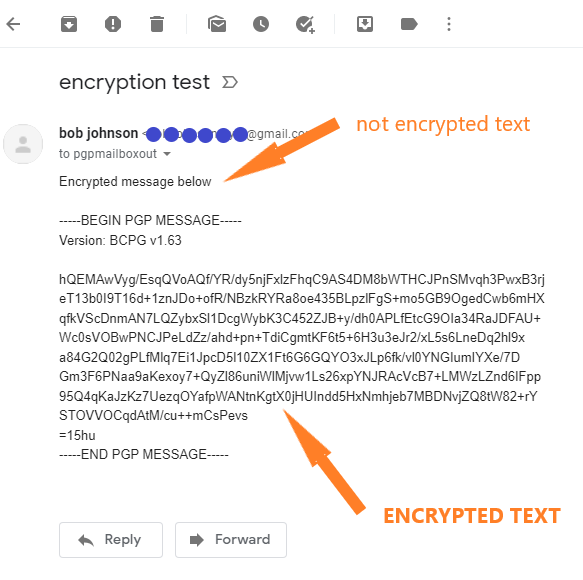
Sending an encrypted email
Before one can send an encrypted email to you, you need to create a key pair – public and private key. The easiest way to do this is by using PGPTool. PGPTool is a java based desktop application which is capable of creating key pairs, encrypting and decrypting message and files.
Creating a key pair
- Download and install PGPTool from: https://pgptool.github.io/
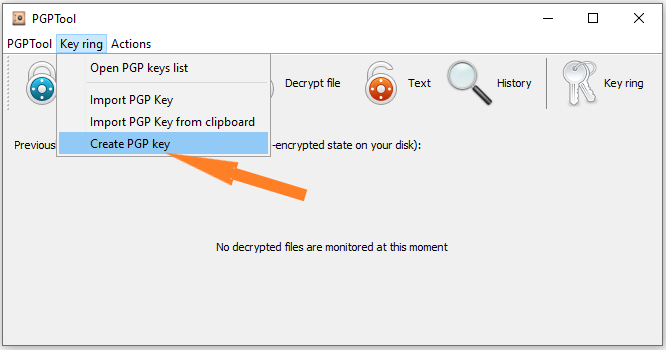
- Create key pair like it shown on the Picture 2 and 3 by going to “Key Ring” > “Create PGP Key”
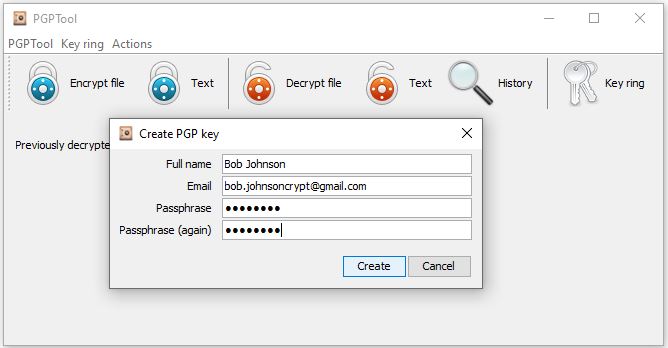
Enter your name, e-mail address and passphrase. Passphrase will be prompted to decrypted message with the private key.
Share Public Key with the senders
Navigate to “Key ring” in order to copy your public key – Picture 4.
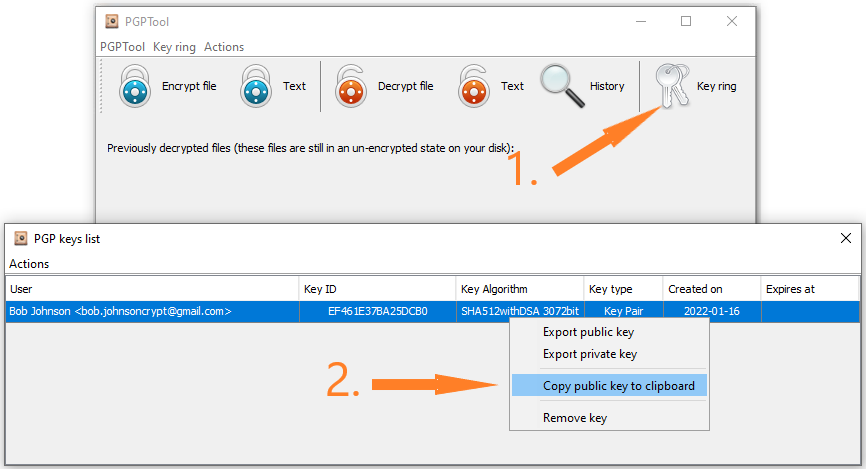
Your Public Key will look something like this. We will use this public key to send encrypted email to our imaginary Bob Johnson.
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: BCPG v1.63
mQSuBGHj9+sRDACmvRnr3fTVxDuGs9k6xyL+MasjoiTAzwfVXvXez1Vrmj94Xw+C
PJihNDtCIFUIqhtClVsDIVJjU30PYea2oiWP6mYaEFFPpBD5RP3wDXjHgsQhDERA
Kphg1BopJ2M+QTnFXQVMeImmxBVAL4sFzGZ7loXwNSbyxbGYVPBSVsS+kTLAJPaX
+AZzOgP7Q6gwB+R4/pKMdAE8zFROlIr0CGlLdXeRaVU/+x9WtBJ+XQlqIU+7zeTz
uGy8cIK/Sh9ZWmWEmyZJxlZx4EAY/G3N08oLof0SjeueqR62VpWskQkGdDs5JWAz
7F5FSRnuAjesMQsLTcuGzoAyt//TSUjGUYWHe7uhWkup1vG3U17fCT+AhExHOAoG
mUJNOB7NtIabDdByd2IPCksYmH890lEbltJw1FxTGEWC30X8HMvg8zltKZtCTAT5
FE6CtThxK53UKfPOk87mld3NmTbPidJDnfnBlF9ihR3UX947iajcu3qcIz2BjmcD
ZOs2uSHQBDw9S+EBAMdn6VTnBwdyw+Jer6T6jiLMrLEiOK/HaaRg/7cA5hIlC/9+
vSGWOIx9BbnR9lfIXieIt35dlqQ1I0VLAam8dBneKeAQYvzHntIJWQxB68nScfj6
nTmXt0HhdgoyeB9h8pmFf+PcTjZ0Sq/HMYNkNuRX8QFaVFcBdGa5vIwAvn7N74in
utLg0sgq85gmsmEY5ywoLD7GMqk0nPUzzrmwub2SB2kGc2hqZEI4osjYQYgUPPrs
cpVUiTQUwXjt6ju8FH5qbvTsANl4AWR0igSOOTTi1v5fQYVY1leYAfbGpe3Y3Sib
jN4twyQku0yHnD0eJmS9jAKG6NGk0RF2JxJN4YKeACW2379J+8sbyMcSqqZ6ev2D
HARtn8CvoesIN+GAAVhZtxJDEG8I/RdT3+1z+3Qtnfoxk4ULnCjb6OFlkKxX0QNJ
Ju0nIlB+eX/fmALqcqMQq3bQYSFnlpF+YSDrY/eClWOaeQynIpSsFBee3w58drw5
2fk+LfdZcaRjiTuJUep8vt9g0YAfb/iM9i74vfUtOejBSeoy2RRM56Mh0HsBTu4L
/jUCq9aItBunKT4B2MwuzLgp4cWlKe2ryJ6kQHDLlSjovFQL98GwFDr9Lhas1XDh
qxfSThZzOBbjx+OPAo1VuazKWQ04kwrOAv0zwrJpZXjyuvvsaJxuBinhkwkn7mki
7B9ihjJb99WM8rBUo7GgDK7SUOtQMW9BLlGtt06GBXL2bLcipKi0bmhr6TZXgt4K
MPsN2kyerbhJXG3ET5U7FbtHLQdZQs3k86jLvhJVdDzp0ZMwqOW+H1vFeQz4EcBX
vrDFUzfYvNyQ7G5/ZrklSkd0VDeWjqh9wAy7tol9gZ3+ZMSmNl2WqtfNBniEtFHE
EoVDuALijpc8OjPFkW3aPw8nkGem/if1Bkw2ufIB4cu5pQIq2hXS3ruy5XO2YdX8
5ShLmiAfMocRQLPDs8qTjxvU2GZ3tOEPt8FKEeYhEgy1pBX3ComY9AYc/Vg+miFT
2a28mqIlhJRUCnhG62pc4lDTURKaDWkXruUiN9N7za/bE44GFUMHgjL67SdF0Z/v
wLQoQm9iIEpvaG5zb24gPGJvYi5qb2huc29uY3J5cHRAZ21haWwuY29tPoheBBMR
CgAGBQJh4/frAAoJEO9GHje6JdywTLEA/0O4K73Ue4rqxc2y++bW7E8bu9TQT+lZ
zOUSBKy8BniLAP4zssyWe5srxVgtrEV03BURyKsyXbfh0LeS3sYmHLimdLkBDQRh
4/frEAQA///////////JD9qiIWjCNMTGYouA3BzRKQJOCIpnzHQCC76mOxObIlFK
CHmONATd75UZs806QxswKwpt8l8UN0/hNW1tUcJF5IW1dmJefsb0TELppjftawv/
XLb0Brft7jhr+1qJn6WunyQRfEsf5kkoZlHs5lOB//////////8AAgID/2p06wMD
4asA3mtrhY//B5khyHweQ648t9s/ZKOQyI949jtks1SjbzDdhGL+7NHHD0TNYKEY
1bCnIGM2+3Oouqus5MY3KhHNIkFqSLVgVZ5qQwSEuI9GrWBaLsyunPrELeUso2mQ
S/U/IT+J2Kki+t5Qu9WU3UvvQ9o0+7xUgVPPiF4EGBEKAAYFAmHj9+sACgkQ70Ye
N7ol3LAwvwD/U8mmB8MIQeEr7CDplReJy8QnBIDtxwhwtd812reGPqgBAKvY142V
CNdc1IwkcW6zNyooZ5hpjgZgpwcESfzRMN0J
=vGxW
-----END PGP PUBLIC KEY BLOCK-----Public key CAN be shared. Simply send it to anybody who wants to send you an encrypted message or file. You can publish your public key in your blog or website, so that people do not need to ask you for the key every time.
Sending an encrypted message
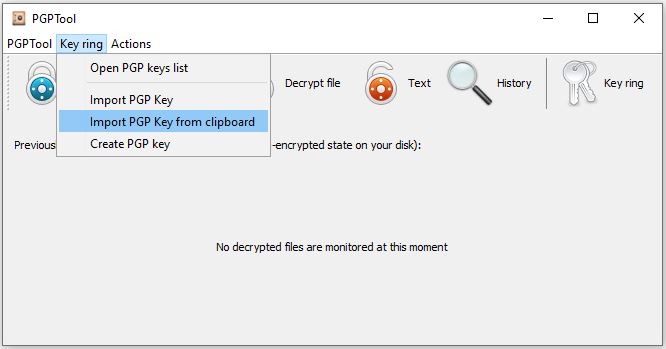
Ok, let’s send our first encrypted email. We will use Public Key we have just created for Bob Johnson and imagine that we want to send an encrypted e-mail to Bob Johnson. First, we need to import public key of the recipient to the PGPTool.
- Copy public key to clipboard (Ctrl+C).
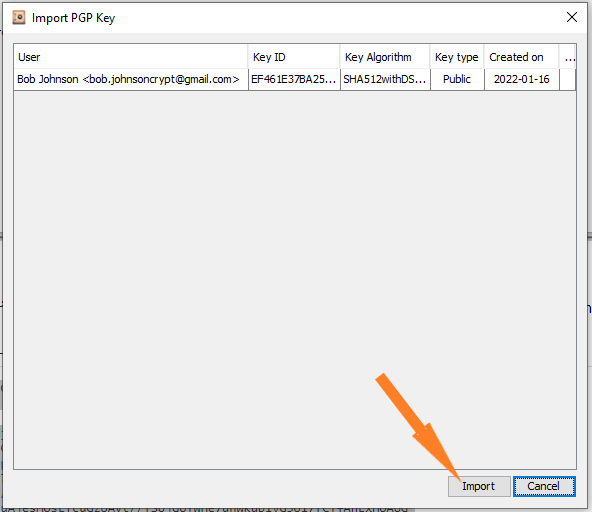
- Import public key into PGPTool – Picture 5 and 6.
3. Encrypt the message with public key
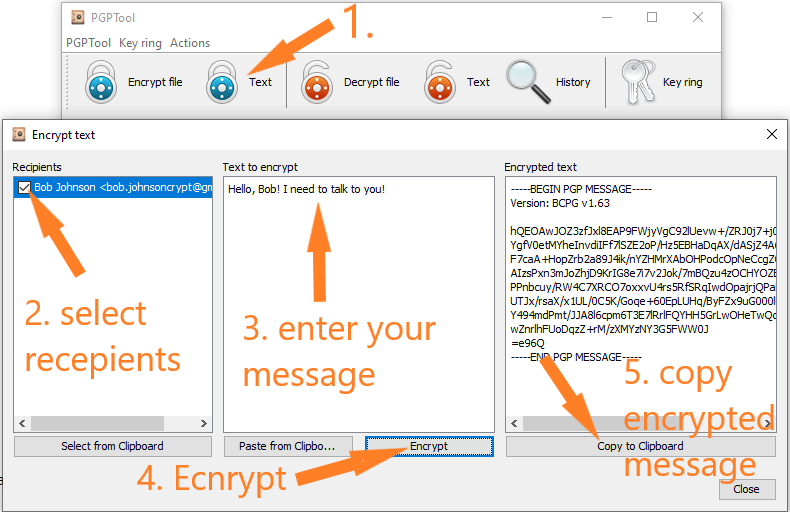
Now we can encrypt our message with Bob Johnson’s public key (Picture 7) and send it in a plain text via any email service provider. Once Bob receives it, he will use his private key to decrypt the message and read it. For encryption go to Text > Select Recipients > Enter message > Press “Encrypt” > Copy encrypted message to clipboard.
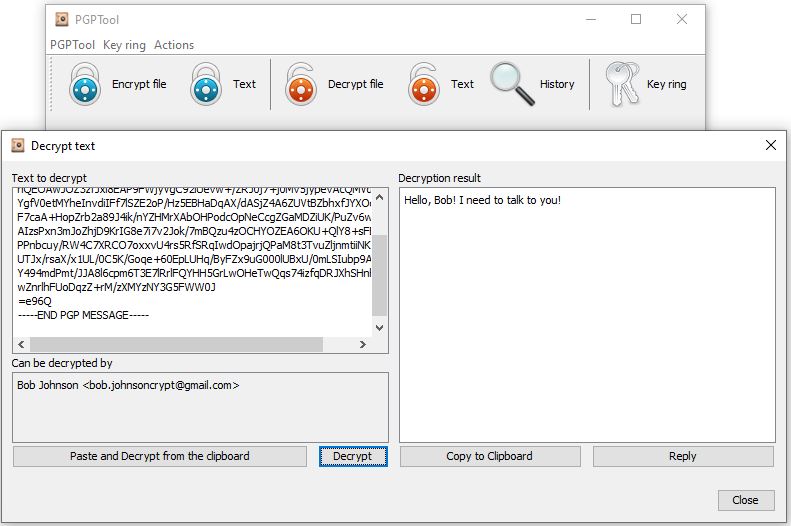
When Bob receives the email containing that weird message, he will know that it’s an encrypted and should be decrypted with his private key. The process is shown on Picture 8.
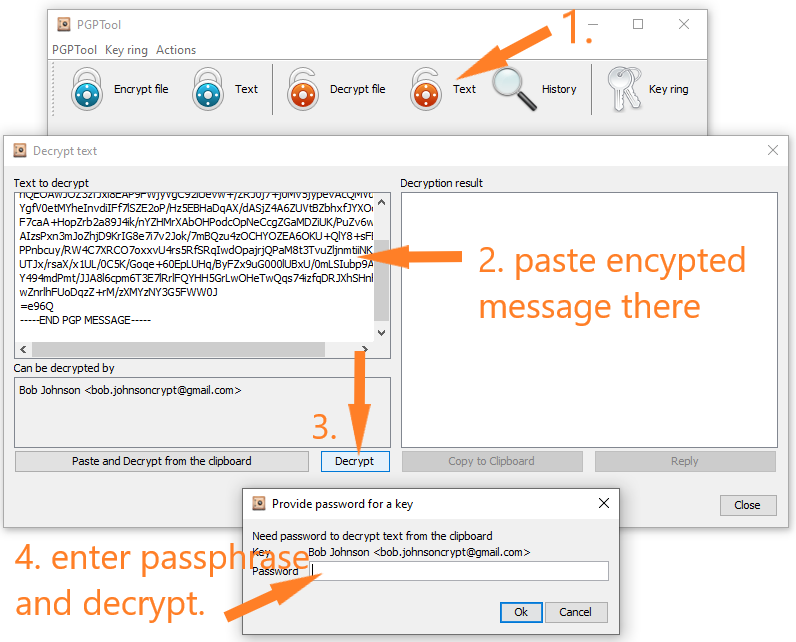
If the passphrase was entered correctly, the original message will show up in the “Decryption result” part of the window (Picture 9). Passphrase is important because it ensures that only authorized person has access to the private key. Otherwise anyone who has the private key can decrypt.
Summary
We have learned how to send and encrypted email. And you can use same software and technique to encrypt regular files as well (we describe it in this article). Let’s summarize sending/receiving of encrypted e-mail.
- Create key pair.
- Obtain public key of the recipient.
- Encrypt your message with the recipient’s public key.
- Attach your public key to the email so that recipient can reply back to you with the encrypted message.
- Send message.
- Decrypt reply with your private key.














